SSH Remote IoT Raspberry Pi: Your Ultimate Guide To Secure Access
When it comes to SSH remote IoT Raspberry Pi, you’re tapping into a game-changing technology that’s transforming how we interact with devices across networks. Imagine having the ability to control and monitor your IoT projects from anywhere in the world, all through a secure connection. It’s like giving your Raspberry Pi a superpower, allowing it to communicate seamlessly with other devices no matter the distance. Whether you’re a tech enthusiast or a professional developer, understanding SSH in the context of IoT and Raspberry Pi is crucial for building robust and secure systems.
In today’s connected world, IoT devices are everywhere, and Raspberry Pi has become one of the most popular platforms for DIY projects and professional applications alike. But with great power comes great responsibility, and that’s where SSH comes in. SSH (Secure Shell) provides a secure way to access and manage your Raspberry Pi remotely, ensuring your data remains safe and your projects stay on track.
This guide dives deep into SSH remote IoT Raspberry Pi, breaking down everything you need to know to set up, secure, and maintain your connections. From beginners to advanced users, this article has got you covered. So, buckle up and let’s explore how SSH can revolutionize your IoT projects!
- Jimmy Fallon Audition The Journey To Becoming A Latenight Legend
- Melanie Joly And Justin Trudeau Relationship The Love Story That Defines Canadian Politics
Table of Contents
- Introduction to SSH Remote IoT Raspberry Pi
- Understanding SSH Basics
- Setting Up SSH on Raspberry Pi
- Securing Your SSH Connection
- Common Issues and Troubleshooting
- Essential Tools for SSH Management
- Applications of SSH in IoT Projects
- Benefits of Using SSH for Remote IoT
- The Future of SSH in IoT
- Conclusion
Introduction to SSH Remote IoT Raspberry Pi
SSH remote IoT Raspberry Pi is all about connecting your Raspberry Pi to the internet securely. It’s like giving your device a personal assistant that helps it communicate with the outside world without compromising its safety. If you’ve ever wondered how to manage your IoT projects from afar, SSH is the answer you’ve been looking for.
Think of SSH as a digital handshake that allows your computer to talk to your Raspberry Pi without anyone eavesdropping. This method ensures that your data stays private and protected, even when you’re accessing your device from a public Wi-Fi hotspot. It’s the ultimate tool for anyone serious about IoT development.
Why SSH Matters
SSH matters because it adds an extra layer of security to your IoT projects. Without it, your data could be vulnerable to hackers and cybercriminals. By using SSH, you’re not only protecting your Raspberry Pi but also ensuring that your IoT devices function smoothly and efficiently.
- Dettol Mould Cleaner Your Ultimate Weapon Against Mold And Mildew
- Does Derek Morgan Come Back A Deep Dive Into The Mind Of A Beloved Character
Understanding SSH Basics
Before diving into the nitty-gritty of SSH remote IoT Raspberry Pi, let’s take a moment to understand what SSH is all about. SSH stands for Secure Shell, and it’s a protocol that provides secure communication between two devices over an unsecured network. It’s like having a secret tunnel that only you and your Raspberry Pi can use.
SSH works by encrypting all data that passes through the connection, making it nearly impossible for anyone to intercept or decipher. This level of security is essential when dealing with sensitive information or controlling critical IoT devices.
How SSH Works
Here’s a quick rundown of how SSH works:
- Authentication: When you connect to your Raspberry Pi via SSH, you need to authenticate yourself using a password or key.
- Encryption: Once authenticated, all communication between your computer and Raspberry Pi is encrypted.
- Connection: You can now control your Raspberry Pi remotely, run commands, transfer files, and more.
Setting Up SSH on Raspberry Pi
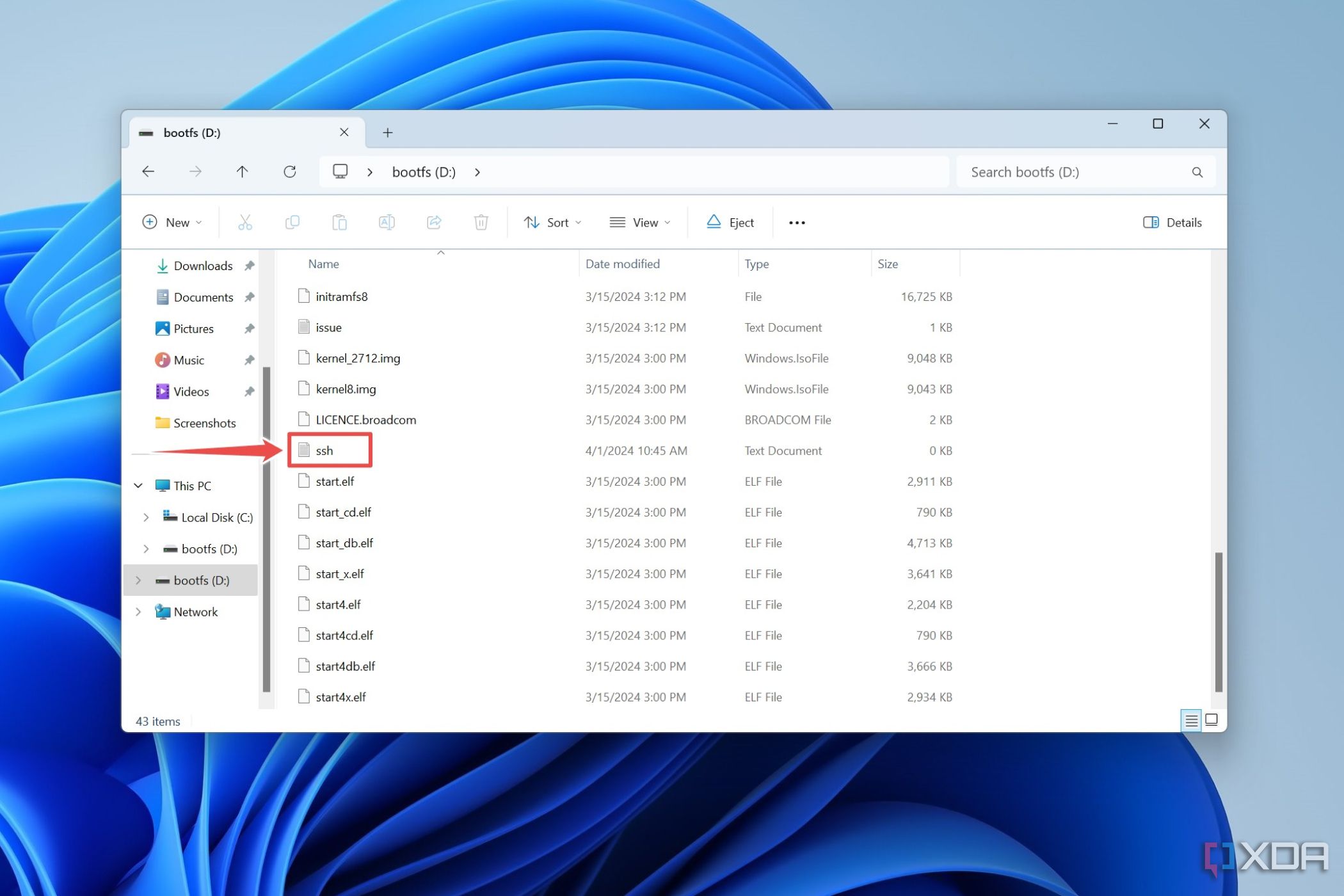
Setting up SSH on your Raspberry Pi is easier than you might think. With just a few simple steps, you can have your device ready for remote access in no time. Here’s how you can do it:
First, make sure your Raspberry Pi is up and running. Then, open the terminal and type the following command:
sudo systemctl enable ssh
This command enables SSH on your Raspberry Pi. Next, you’ll want to configure your network settings to ensure your Raspberry Pi has a static IP address. This way, you can always connect to it using the same address, even if your network changes.
Configuring SSH
Once SSH is enabled, you can configure it to suit your needs. For example, you can set up SSH keys for passwordless login or restrict access to specific users. These configurations help enhance the security of your SSH connection and protect your Raspberry Pi from unauthorized access.
Securing Your SSH Connection
Security is paramount when it comes to SSH remote IoT Raspberry Pi. While SSH provides a secure connection by default, there are additional steps you can take to make it even more secure. Here are a few tips:
- Use Strong Passwords: Always use strong, unique passwords for your SSH login.
- Enable SSH Keys: SSH keys provide a more secure method of authentication compared to passwords.
- Change Default Port: Changing the default SSH port can deter automated attacks.
- Install a Firewall: A firewall can help block unauthorized access attempts.
Advanced Security Measures
For those looking to take their security to the next level, consider implementing two-factor authentication (2FA) for SSH. This adds an extra layer of protection by requiring a second form of verification in addition to your password or key. Another option is to use fail2ban, a tool that automatically blocks IP addresses that exhibit suspicious behavior.
Common Issues and Troubleshooting
Even with the best setup, issues can arise. Here are some common problems you might encounter when using SSH remote IoT Raspberry Pi and how to troubleshoot them:
- Connection Refused: If you can’t connect to your Raspberry Pi, check your network settings and ensure SSH is enabled.
- Permission Denied: This usually means there’s an issue with your authentication method. Double-check your password or key.
- Timeout Errors: These can occur if your network is unstable or if your Raspberry Pi is overloaded. Try restarting your device or improving your network connection.
Debugging Tips
When troubleshooting SSH issues, it’s helpful to use the verbose option to get more detailed error messages. You can do this by adding the -v flag to your SSH command:
ssh -v user@raspberrypi
This will provide more information about what’s going wrong, helping you diagnose and fix the problem more effectively.
Essential Tools for SSH Management
Managing SSH connections can be made easier with the right tools. Here are a few essentials you should consider:
- SSH Clients: Tools like PuTTY (for Windows) or Terminal (for macOS and Linux) allow you to connect to your Raspberry Pi via SSH.
- SSH Key Generators: These tools help you create secure SSH keys for passwordless login.
- Monitoring Software: Programs like Nagios or Zabbix can monitor your SSH connections and alert you to any issues.
Choosing the Right Tool
When selecting tools for SSH management, consider your specific needs and the complexity of your IoT projects. For beginners, simple tools like PuTTY or Terminal might be sufficient. However, as your projects grow, you may want to invest in more advanced tools that offer additional features and functionality.
Applications of SSH in IoT Projects
SSH has countless applications in IoT projects. From remote monitoring and control to secure data transfer, SSH is a versatile tool that can enhance almost any IoT setup. Here are a few examples:
- Home Automation: Use SSH to control smart home devices like lights, thermostats, and security systems from anywhere.
- Industrial IoT: SSH can be used to monitor and manage industrial equipment, ensuring smooth operations and reducing downtime.
- Environmental Monitoring: Deploy SSH-enabled sensors to collect data on air quality, temperature, and humidity in remote locations.
Real-World Examples
One real-world example of SSH in IoT is in agriculture, where farmers use SSH-enabled sensors to monitor soil moisture levels and automate irrigation systems. This not only saves time but also improves crop yields by ensuring plants receive the right amount of water.
Benefits of Using SSH for Remote IoT
The benefits of using SSH for remote IoT Raspberry Pi are numerous. Here are just a few:
- Security: SSH provides a secure connection, protecting your data and devices from unauthorized access.
- Convenience: With SSH, you can manage your IoT projects from anywhere, as long as you have an internet connection.
- Flexibility: SSH allows you to run commands, transfer files, and perform a wide range of tasks remotely.
Why Choose SSH Over Other Protocols?
Compared to other protocols like Telnet, SSH offers superior security and reliability. While Telnet is faster and simpler, it lacks the encryption and authentication features that make SSH so valuable for IoT applications.
The Future of SSH in IoT
As IoT continues to evolve, the role of SSH in securing and managing these devices will only grow. With advancements in technology, we can expect SSH to become even more powerful and versatile, enabling new and exciting applications in fields like healthcare, transportation, and smart cities.
Looking ahead, the integration of SSH with emerging technologies like blockchain and artificial intelligence could revolutionize how we approach IoT security and management. These developments promise to make SSH an even more indispensable tool for IoT developers and enthusiasts alike.
Trends to Watch
Some trends to keep an eye on include the rise of quantum-resistant encryption methods and the increasing use of machine learning to detect and respond to security threats in real-time. These advancements will undoubtedly shape the future of SSH in IoT and beyond.
Conclusion
In conclusion, SSH remote IoT Raspberry Pi is a powerful and essential tool for anyone working with IoT devices. By understanding how SSH works and implementing best practices for security and management, you can unlock the full potential of your IoT projects and ensure they remain safe and efficient.
We encourage you to take what you’ve learned and apply it to your own projects. Whether you’re setting up SSH for the first time or looking to enhance your existing setup, the possibilities are endless. Don’t forget to share your experiences and tips in the comments below, and be sure to check out our other articles for more insights into the world of IoT and Raspberry Pi.
Happy tinkering, and stay secure out there!
- Lucas Mom The Ultimate Guide To Understanding The Phenomenon And Its Impact
- What Is Dere Definition The Ultimate Guide To Understanding Dere In Everyday Context

Raspberry Pi How to enable SSH
How to SSH into Raspberry Pi for Remote Access on Windows
Unlocking The Power Of Remote Ssh Raspberry Pi A Comprehensive Guide